Bug Bounty @ Microsoft
My first vulnerability within Microsoft with $$$
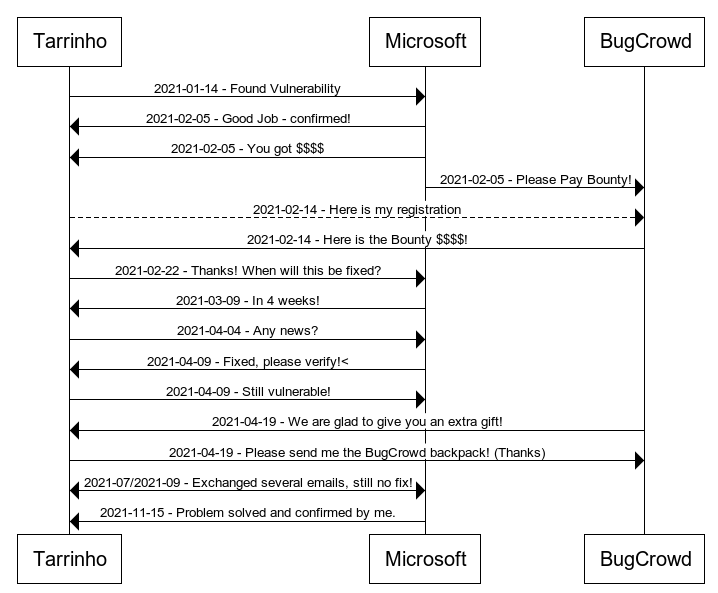
I just found a vulnerability within Microsoft landscape and decided to see how did the Microsoft Security Response Center works, and if I could receive some $$$ for finding it.
-
Goal: Find a vulnerability within Microsoft! - check (2021-01-xx)
-
Goal: Submit that vulnerability to
 - check (2021-01-14)
- check (2021-01-14) -
Goal: Get confirmation from Microsoft - check (2021-02-05)
-
Goal: Got Bounty $$$$
- check (2021-02-16)
-
Goal: Have Microsoft fix it, so I can publish my finding - pending (expected - ???? )
-
Extra: Got a backpack from Bugcrowd! (Thanks!)
-
Status (2021-04-09) - Got confirmation that this vulnerability was fixed! Just confirmed that it is NOT fixed! New email sent to Microsoft, waiting response!
-
(2021-07-07) - Exchanged several emails asking for status, still no fix!**
-
Conclusion (2021-11-15) - Got reply from MSRC that issue was fixed and nothing else will be done. Replied back accepting their confirmation and givin notice that I will be sharing my finding. Double checked that the standard attack approach isn’t valid.
-
Steps in Detail!